In an increasingly intricate threat environment, complete peace of mind is your top priority. Count on IT Support Leaders to safeguard your network and sensitive data against the intensified challenges of AI-powered cyberattacks and increased mobility.
Our team of cybersecurity experts excels at deploying a comprehensive, multi-layered security solution. We utilize top-tier tools, vigilant monitoring, and proactive measures, and our swift incident response system ensures any breach is quickly contained and mitigated.
Beyond protection, we prioritize business continuity. In the event of a cyber incident, our strategic recovery planning helps keep your operations running smoothly, minimizing downtime and ensuring your business thrives under any circumstances. Trust IT Support Leaders to keep your organization secure, resilient, and ready for growth.

In an increasingly intricate threat environment, complete peace of mind is your top priority. Count on IT Support Leaders to safeguard your network and sensitive data against the intensified challenges of AI-powered cyberattacks and increased mobility.
Our team of cybersecurity experts excels at deploying a comprehensive, multi-layered security solution. We utilize top-tier tools, vigilant monitoring, and proactive measures, and our swift incident response system ensures any breach is quickly contained and mitigated.
Beyond protection, we prioritize business continuity. In the event of a cyber incident, our strategic recovery planning helps keep your operations running smoothly, minimizing downtime and ensuring your business thrives under any circumstances. Trust IT Support Leaders to keep your organization secure, resilient, and ready for growth.



Robust Security - Our approach integrates a sophisticated multi-layered security solution stack. It incorporates constant monitoring, accurate detection, and rapid response mechanisms to safeguard your business comprehensively.

Simplicity - A powerful security framework can coexist with a seamless user experience. Our security measures enhance, rather than burden, your daily operations, ensuring your team interacts with an intuitive, unobtrusive system. At IT Support Leaders, we harmonize security and simplicity for a balanced and efficient business environment.
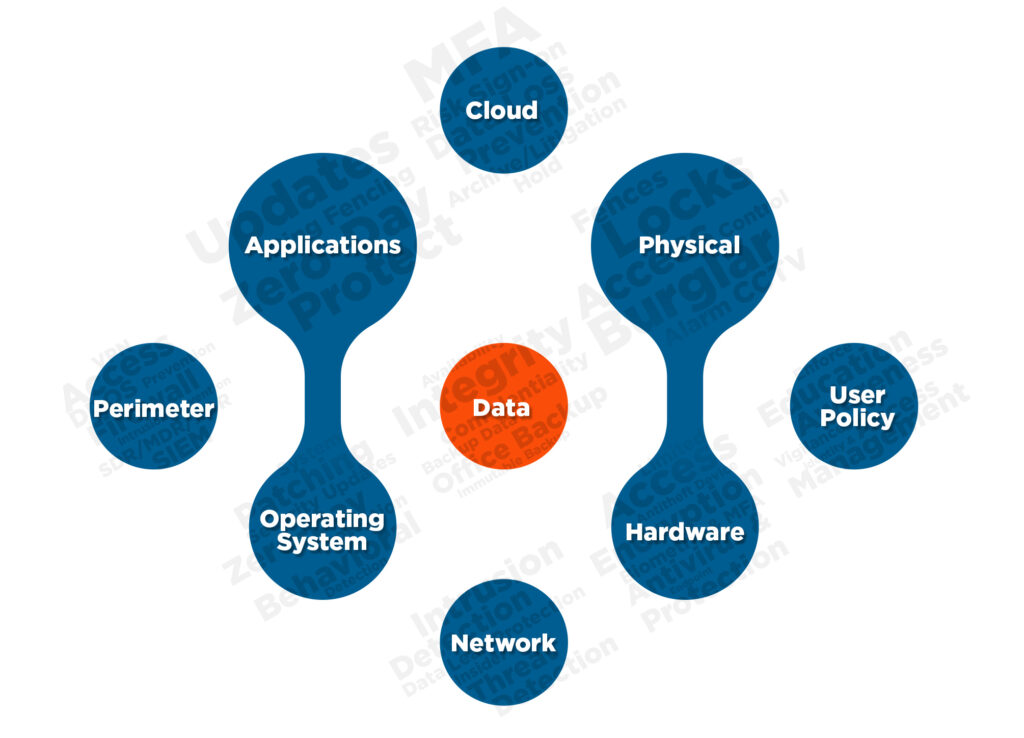
Our Holistic Security Approach – Guarding All Fronts
Our comprehensive, multi-layered security strategy: At its core is your valuable data, surrounded by an array of robust protective layers.
Starting from the outermost layer, Perimeter Security, we build defenses against threats before they reach your network. Next, we secure the Operating System layer, providing safeguards against vulnerabilities at the very heart of your systems.
In the Application layer, we implement security measures to protect your specific software. Network security ensures that the connections between your systems are fortified. In the Cloud layer, we apply robust security protocols to defend your cloud-based resources.
At the Hardware level, we safeguard your physical equipment from cyber threats. In the Physical layer, we address the security of your tangible assets, like your server rooms and equipment. Finally, the User Policy layer encompasses guidelines and procedures to ensure that your employees follow best security practices.
Each of these layers is equally important in creating a holistic security approach, ensuring that every aspect of your organization’s IT environment is fortified against potential cyber threats. This multi-layered strategy provided by IT Support Leaders encapsulates the essence of robust, comprehensive cybersecurity.
Our Team works hard behind the scenes to harden your security at every layer so that your users have a seamless experience while you have the peace of mind knowing that a world-class security stack and our Team of experts is protecting your business and your sensitive data.
A multi-layered cyber security architecture is essential for businesses of all sizes. It helps protect your organization from a wide range of cyber threats including malware, phishing attacks, ransomware, and can help you comply with regulatory requirements and protect your operations and reputation.